Bgp Hijacking Rpki, 2
In 2020 the Internet was a lifeline for many people across the world as COVID-19 shifted schools and businesses online. A successful hijack can make a domains name servers unreachable or cause DNS queries to be diverted to malicious servers.
Bgp Rpki Mit Xr7 Cisco8000 Whitepaper Cisco
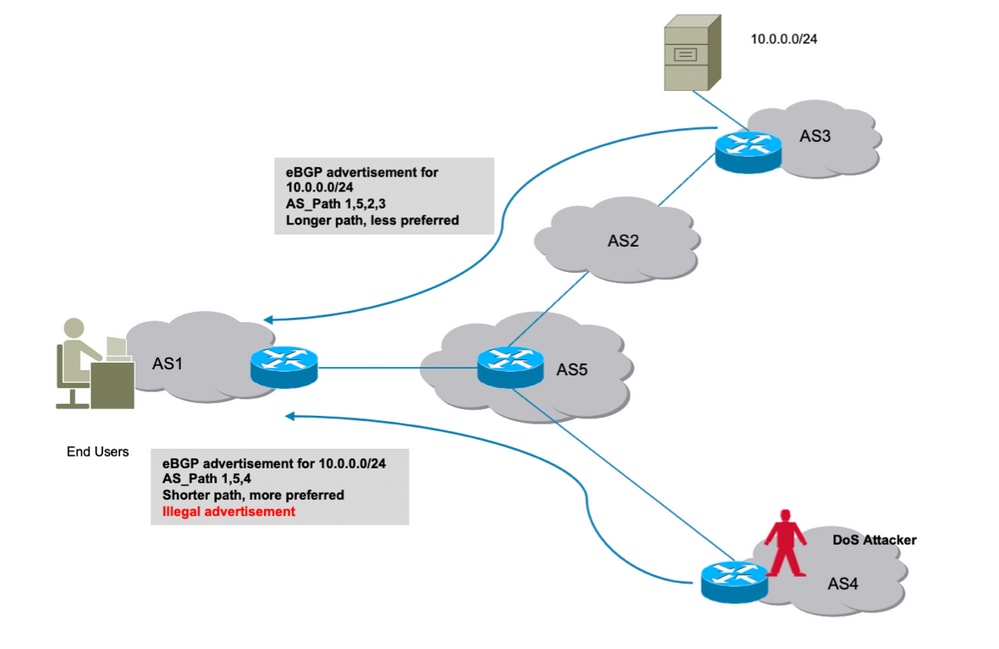
The hijackers BGP announcement is valid according to the RPKI since the ROA 1921680016-24 AS 64496 authorizes AS 64496 to originate BGP routes for 1921680024 Because AS 64496 does not actually originate a route for 1921680024 the hijackers route is the only route to the 1921680024.
Bgp hijacking rpki. This article will talk about our approach to network security using technologies like RPKI to sign Internet routes and protect our users and customers from route hijacks and misconfigurations. Without addressing these vulnerabilities either through RPKI or stopgap measures BGP hijacking will be able to continue unabated. While RPKI isnt perfect at preventing BGP hijacking almost half of all networks employing the tool are less susceptible to route leaks according to Cloudflares tests.
But as theres a saying if you always do what you always did you will always get what you always got. The numerous endeavors to secure the routing infrastructure of the internet evolved into a specialized public key infrastructure. Aircraft hijacking the unlawful seizure of an aircraft by an individual or a group.
This time well explain how to mitigate some of the most common routing problems by using RPKI. Primarily for people without network experience. Use this tutorial to better understand the complex world of BGP and learn some simple and advanced BGP troubleshooting steps.
In its early days BGP didnt include any method to. Role of big players is crucial. 2018 - Pembajakan prefix BGP untuk pencurian matauang cryptocurrency.
2008 - ISP di pakistan yang berusaha memblokir youtube dengan membajak BGP menyebabkan youtube tidak bisa diakses hampir di seluruh dunia. Another term used to refer to RPKI is Resource Certification. Left unchecked a BGP route hijack or leak can cause a.
BGP RPKI and MANRS. Although the BGP hijacking incidents in 2020 encouraged Cloudflare to launch a Is BGP safe yet service that lets Internet users know if their ISP has upgraded its BGP security and Google plans to redouble its efforts as a MANRS partner to fix BGP faster experts say that we are years away from universal RPKI adoption. BGP RPKI and MANRS.
This key is known as RPKI Resource Public Key Infrastructure. Im aware of multiple initiatives among the big providers to produce consume RPKI data. BGP Hijacking dengan adanya RPKI.
2017 - Pembajakan prefix Visa Mastercard yang menyebabkan proses perbankan terganggu. As the initial protocols at the core of the internet are not sufficiently secure for the scope and threat landscape it has reached since ever new security patches are being applied. Sometimes misconfigurations Like accidentally announcing a wrong prefix can break the internet.
BGP and RPKI. Once RPKI is enabled and active on the Lumen network for both peer and customer BGP sessions there will be no requirement or process to order RPKI because it will already be on. Enabling RPKI on the Lumen AS3356 internet core.
BGP stands for Border Gateway Protocol more commonly known as the system that keeps the internet and by definition routing working correctly. Last month as reported by BleepingComputer one of Americas largest broadband providers Comcast implemented RPKI on its network to block BGP hijacking attacks and leaks. RPKI provides a step in securing BGP routing.
It was only logical then that we would see an increase in Internet usage across the globe. Comcast one of Americas largest broadband providers has now deployed RPKI on its network to defend against BGP route hijacks and leaks. It is the language spoken by routers to determine how packets can be sent from one router to another to reach their final destination.
NTT is working to plan out RPKI Origin Validation trials with select partners we want to carefully dip our toe into the water. Implementing BGP filters on external BGP sessions Adding a policy to all BGP sessions peer transit and customers to reject any prefix that is RPKI Invalid. This recent hijack may be the event that tipped the scale and encourages the big providers to start protecting each other.
RPKI and BGP. In our first post we explained BGP hijacking and route leaks. A Path Made Clear with Kentik.
Most router software and environments have RPKI. This article originally appeared on APNIC which has kindly let us repost it. RPKI and the DNS.
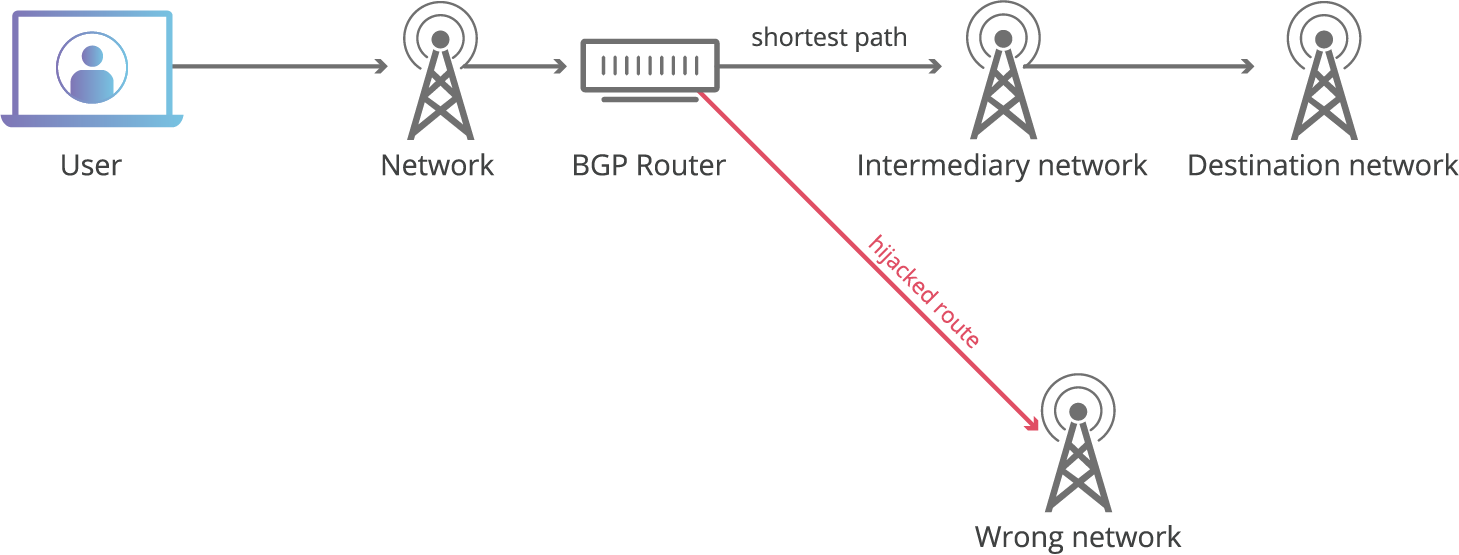
Routing hijacks are a threat to the availability and reliability of the DNS and other services. Why RPKI wont save BGP. RPKI to Tackle Route Hijacking and Leaks.
In this blog post I will explain BGP Hijacking and how to prevent it. And configuration errors or fat fingers can have much the same effect as. Our path to securing Internet Routing.
It was only logical then that we would see an increase in Internet usage across the globe. Dec 09 2020 A BGP route leak is the propagation of routing announcements beyond their intended scope. Mitigating prefix hijacks with RPKI Part 2 By Tiziano Tofoni CEO of Reiss Romoli Flavio Luciani CTO of Namex Roma IXP MANRS ambassador and Hiba Eltigani MANRS fellow.
RPKI validates the correctness of origin AS stopping stupid fat-finger mistakes like two-way BGP-OSPF-BGP redistribution misconfigured BGP optimizers bringing down third-party services due to clueless tier-1 provider or the spillover effects of third-world countries trying to stop their population from watching unorthodox video. In 2020 the Internet was a lifeline for many people across the world as COVID-19 shifted schools and businesses online. As Fastly highlighted in this blog post the global rise in Internet demand was indeed dramatic.
Border Gateway Protocol more commonly known as BGP is the routing protocol that makes the internet work. We are proud to announce we have started deploying.
Rpki And Bgp Our Path To Securing Internet Routing
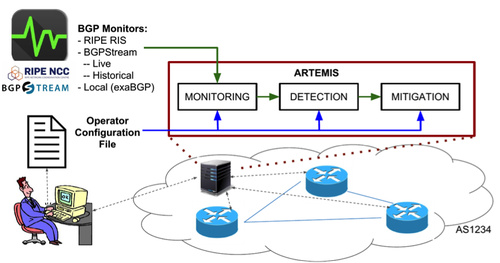
Artemis Neutralising Bgp Hijacking Within A Minute Ripe Labs

How Aws Is Helping To Secure Internet Routing Networking Content Delivery

Bgp Hijackings Come Back Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks
Rpki And Bgp Our Path To Securing Internet Routing
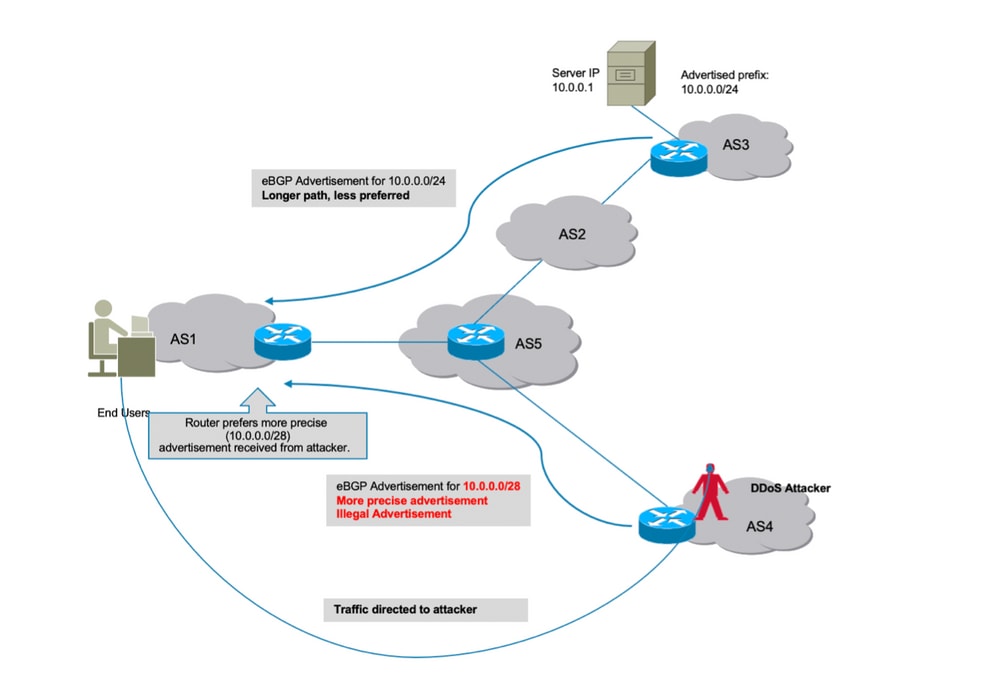
Bgp Rpki Mit Xr7 Cisco8000 Whitepaper Cisco
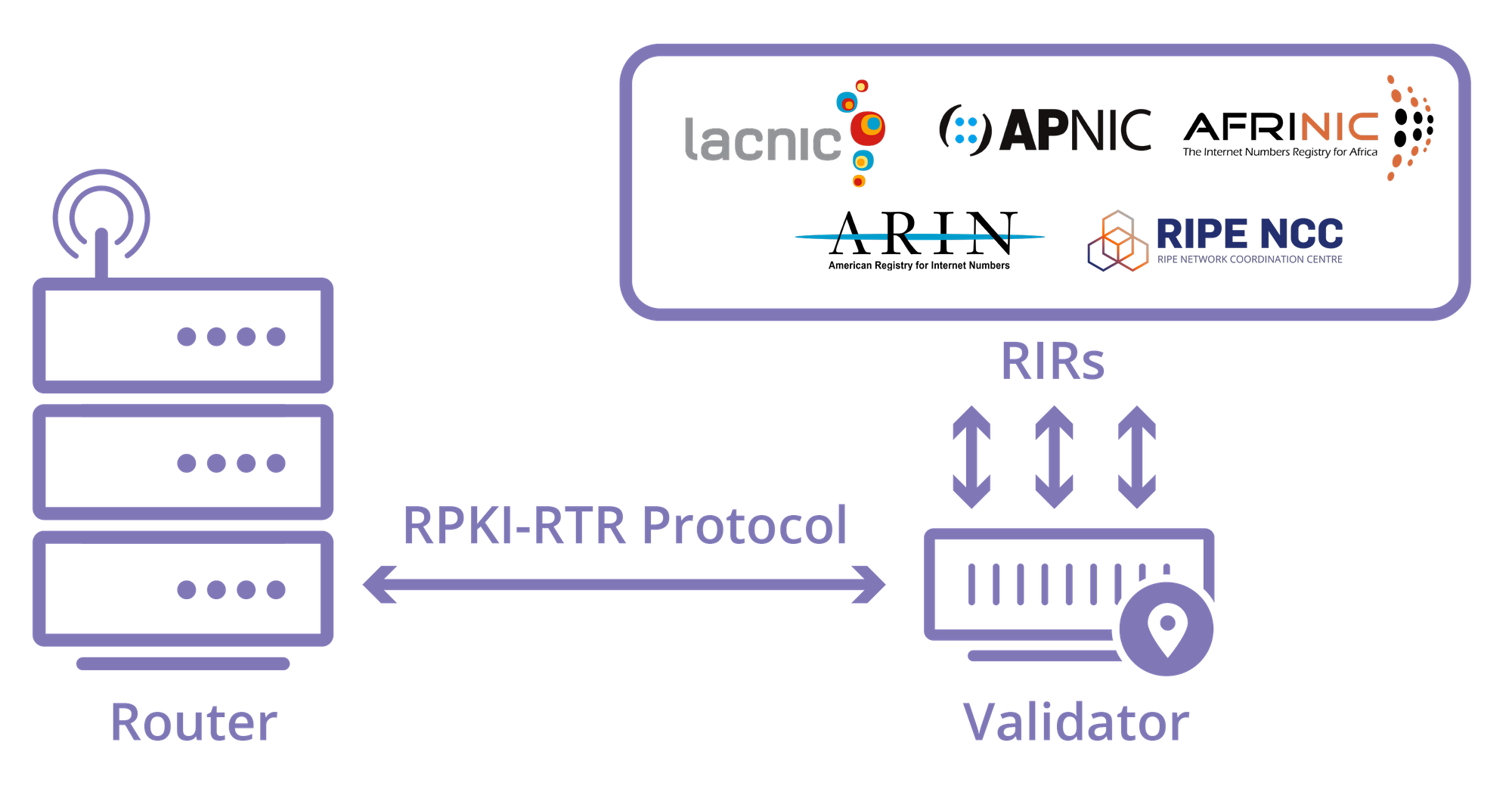
Rpki And Bgp Our Path To Securing Internet Routing
Comcast Now Blocks Bgp Hijacking Attacks And Route Leaks With Rpki

How Aws Is Helping To Secure Internet Routing Networking Content Delivery
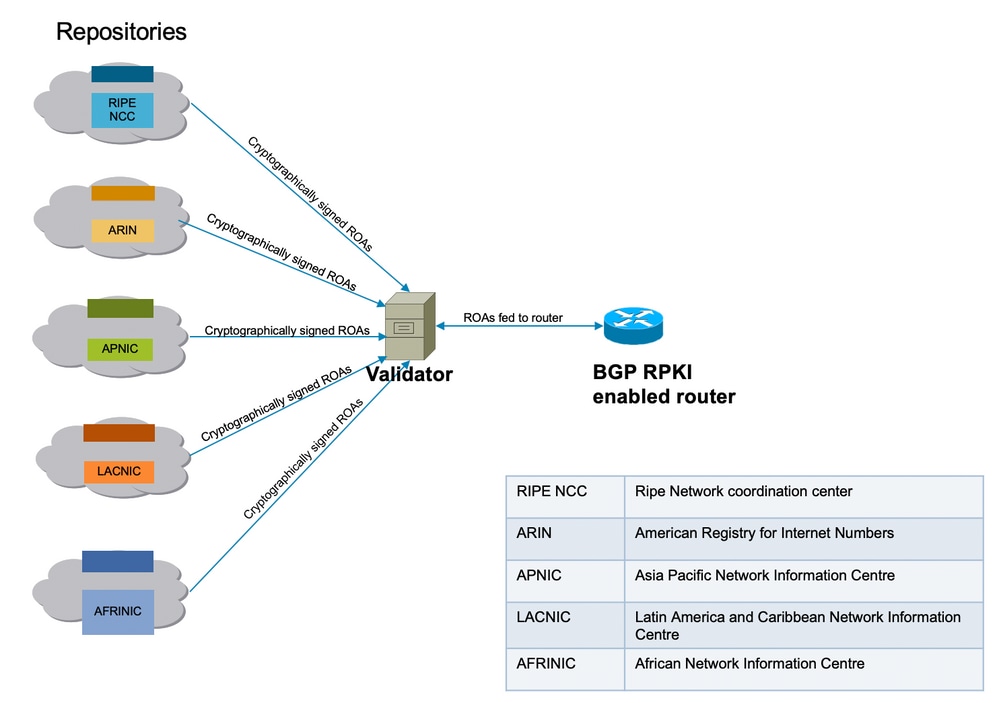
Bgp Rpki Mit Xr7 Cisco8000 Whitepaper Cisco

Mitigating Prefix Hijacks With Rpki Part 2

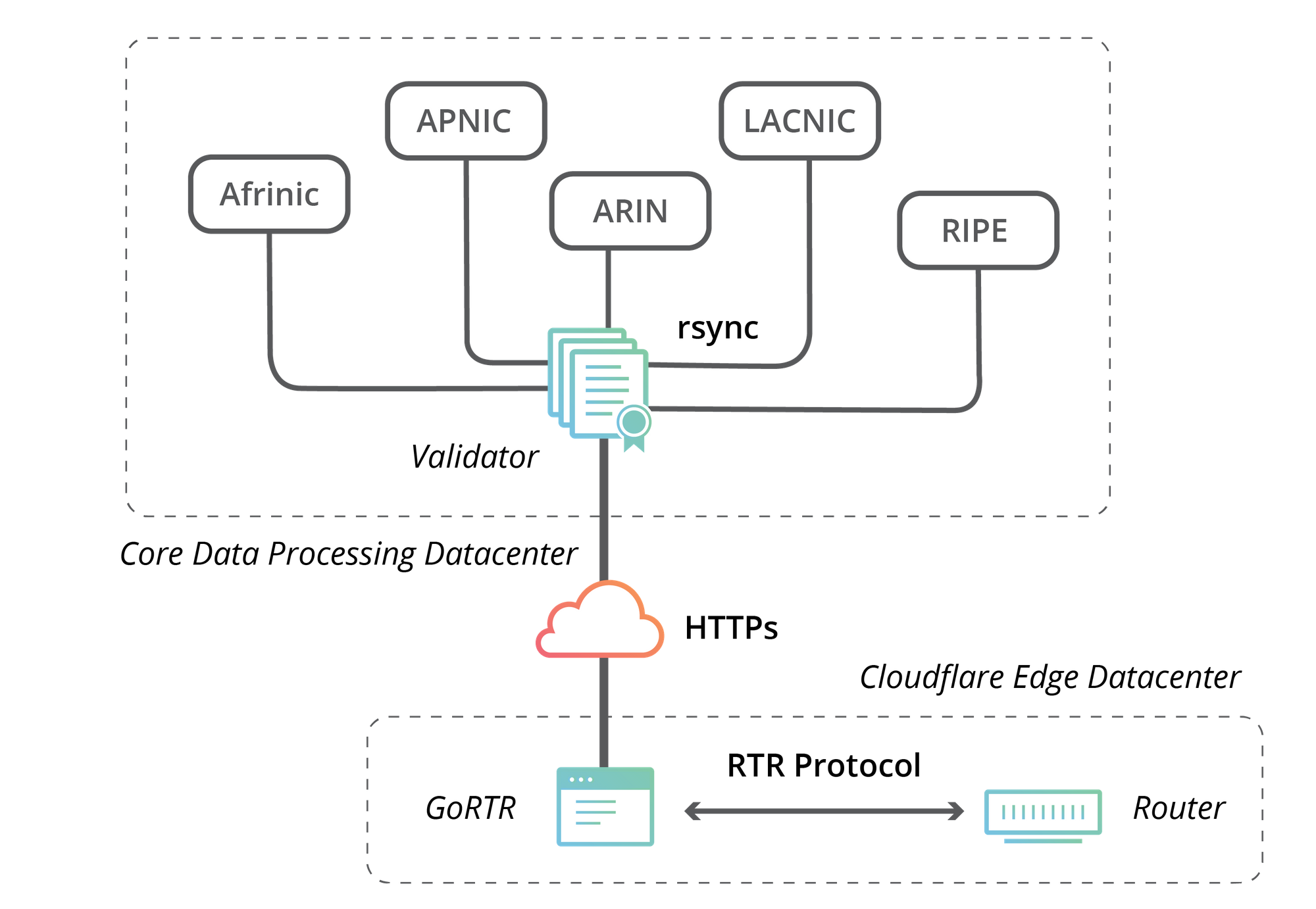
A Local Cache Syncs With Rpki Publication Points Bgp Routers Download Scientific Diagram
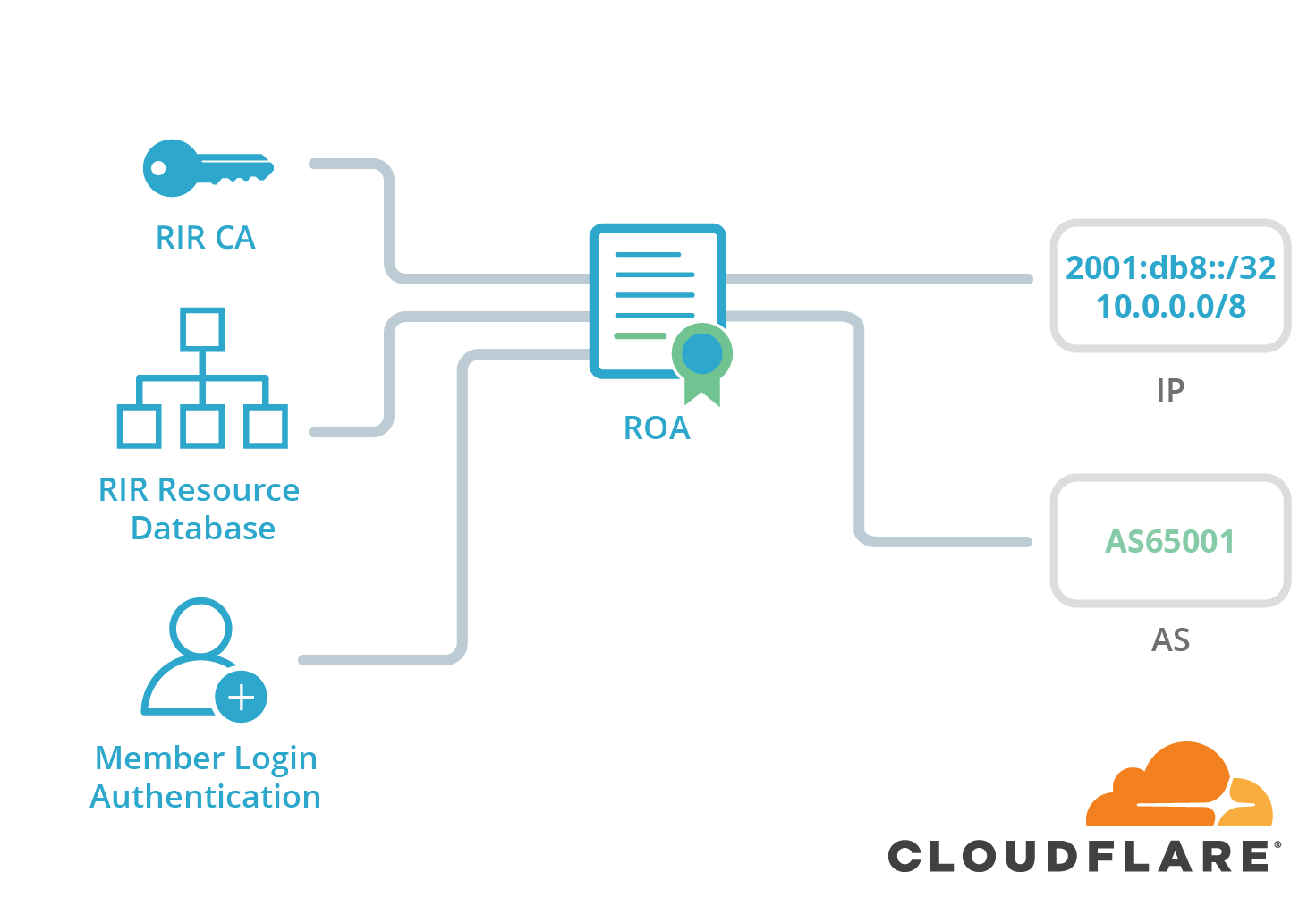
Rpki And Bgp Our Path To Securing Internet Routing
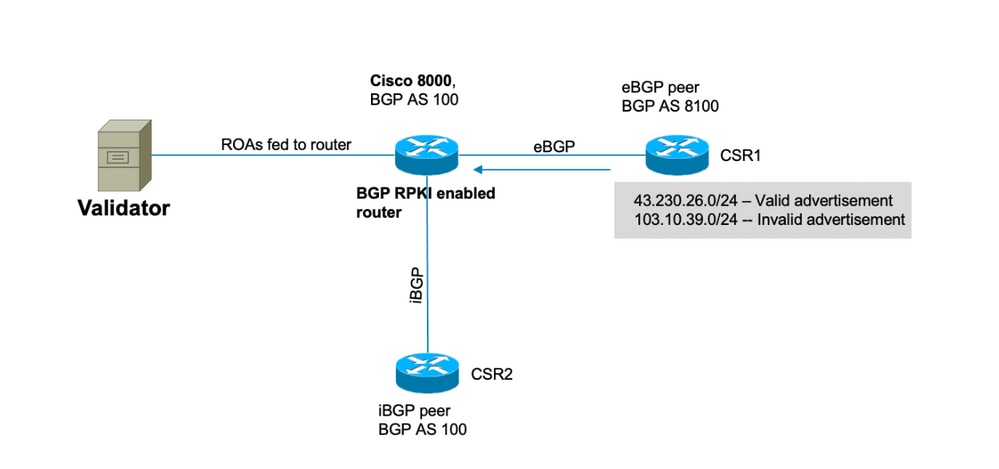
Bgp Rpki Mit Xr7 Cisco8000 Whitepaper Cisco
A Local Cache Syncs With Rpki Publication Points Bgp Routers Download Scientific Diagram
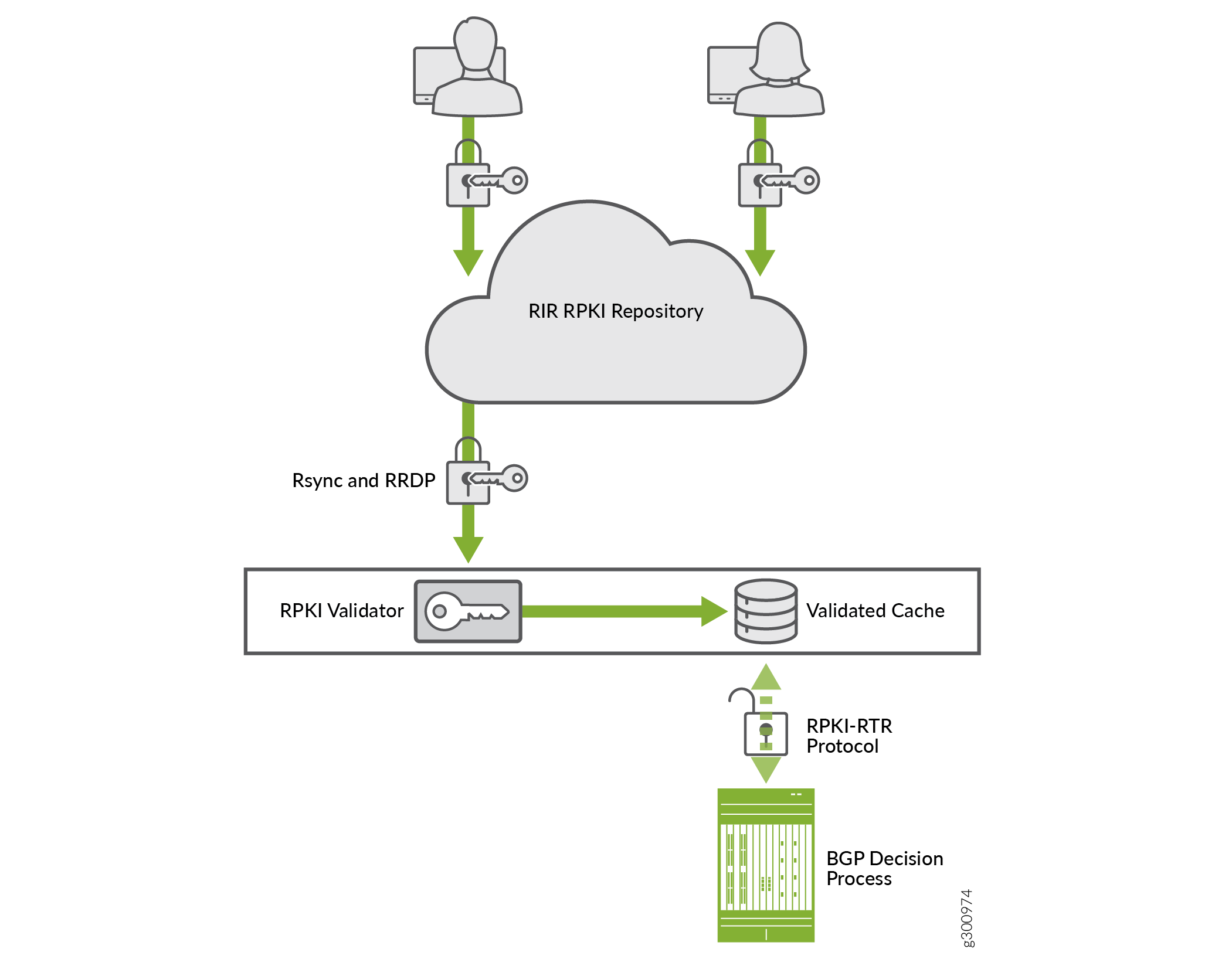
Technical Overview Techlibrary Juniper Networks
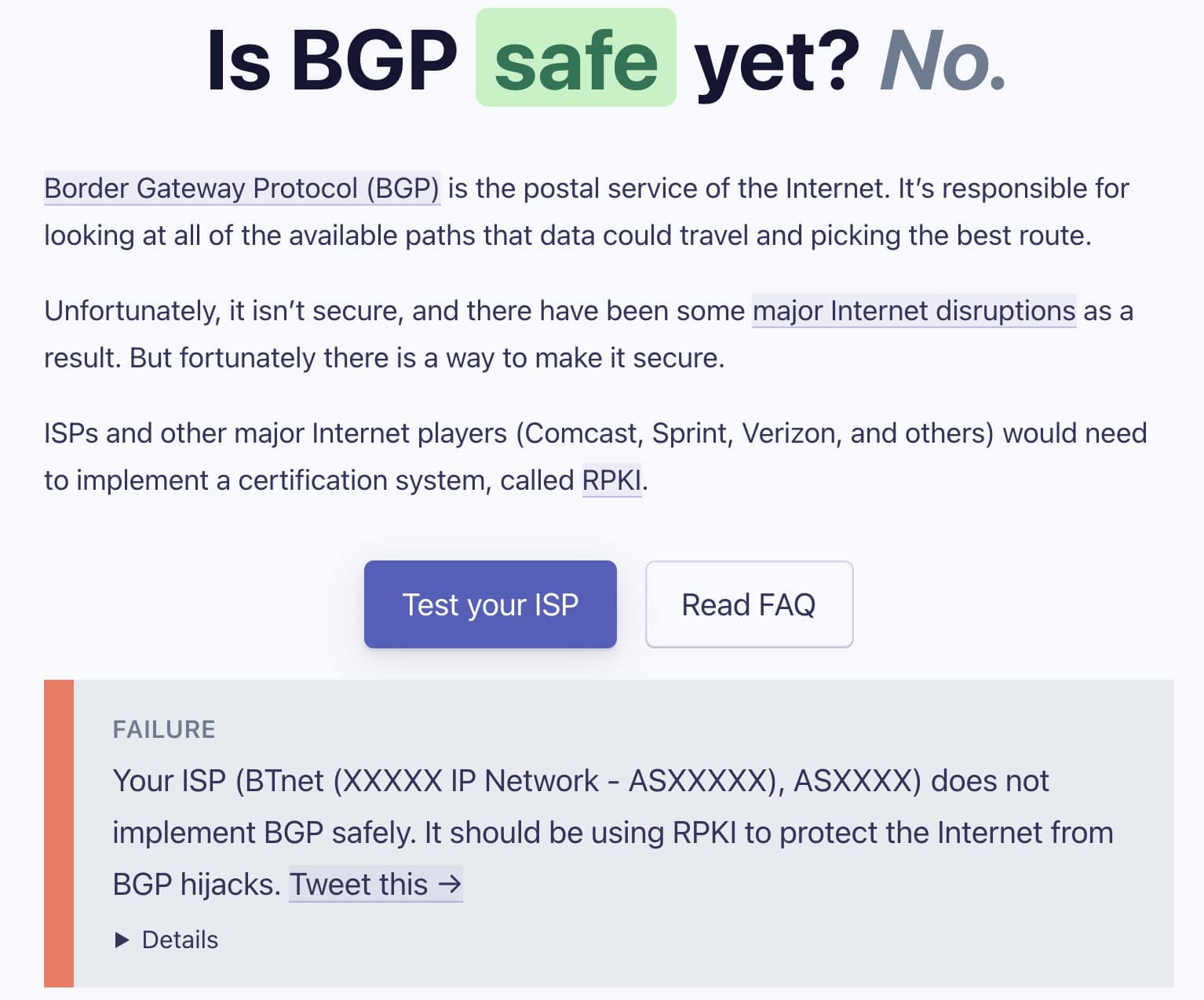
Comcast Now Blocks Bgp Hijacking Attacks And Route Leaks With Rpki
Principle Bgp Hijacking Risk Reduction Is A Layered Solution Senki